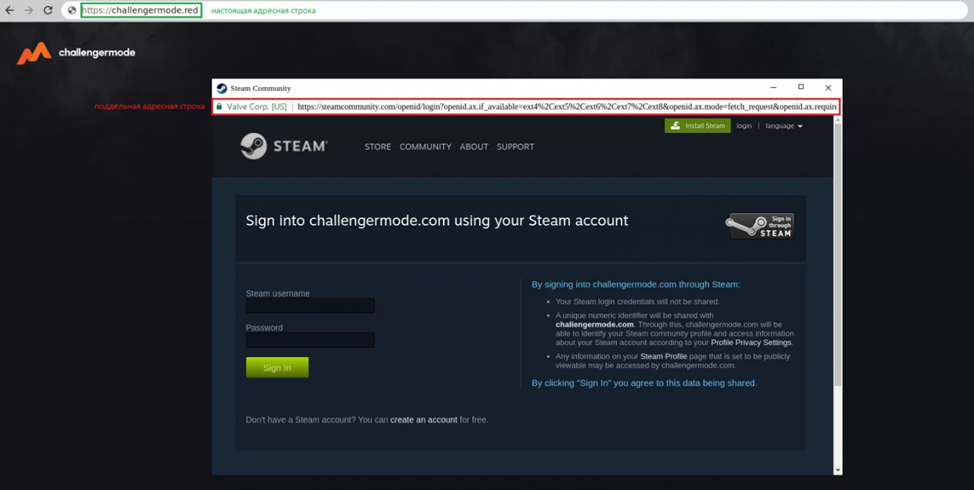
Steam users have been targeted by hackers using Browser-in-the-Browser (BiTB) phishing attacks to steal their credentials.
The new attack method includes developing a fake browser window within an active window to mimic a sign-in page for a particular login service. The phishing kit isn’t easily procurable on hacking forums or the dark web. Instead, hackers use Discord or Telegram channels to gain easy access to the new phishing kit. Threat actors intend to sell access to these hacked accounts, starting from $100,000 to $300,000.
The targets are sent direct invitation links on their Steam account, requesting them to join a team for LoL, CS, Dota 2, or PUBG competitions. Once the link is clicked, they are directed to a phishing site organizing esports competitions.
An attack is a novel phishing technique that replicates pop-up windows used for SSO in an effort to steal login credentials. It works like this[:] The cybercriminals register a website using the classic phishing technique of making a clone of a legitimate website
Term used for a broad range of malicious activities accomplished through human interactions
References on how to protect yourself from scamming: